Cyber Security
Cybersecurity services encompass a variety of offerings designed to protect IT systems, networks, and data from cyber threats. Here are some key categories of cybersecurity services that businesses can utilize:







Secure & Insure
Your Digital Assets

Vulnerability Assessments: Identifying security vulnerabilities in a system or network.
Penetration Testing: Simulated cyber attacks to test the effectiveness of security measures
Security Audits: Comprehensive evaluations of an organization's adherence to regulatory guidelines and security policies.
Firewall Management: Installation, maintenance, and monitoring of firewall configurations.
Intrusion Detection and Prevention Systems (IDPS): Monitoring network traffic to detect and respond to malicious activity.
Virtual Private Network (VPN) Management: Ensuring secure remote access through encrypted connections.
Antivirus and Anti-malware Solutions: Protection against malware, ransomware, and other threats.
Mobile Device Management (MDM): Securing and managing mobile devices accessing organizational resources.
Patch Management: Ensuring software is up-to-date with the latest security patches.
Multi-factor Authentication (MFA): Enhancing security by requiring multiple methods of authentication.
Single Sign-On (SSO): Streamlining the authentication process across various systems.
Privileged Access Management (PAM): Controlling and monitoring privileged user access.
Encryption Services: Protecting data by converting it into a secure format.
Data Loss Prevention (DLP): Monitoring and controlling data to prevent unauthorized access or breaches.
Backup and Disaster Recovery: Ensuring data is securely backed up and can be recovered after a disaster.
Managed Detection and Response (MDR): Ongoing monitoring and response to cybersecurity threats.
Security Operations Center (SOC) as a Service: Outsourcing the management of a security operations center.
Managed Security Information and Event Management (SIEM): Real-time analysis and reporting of security alerts generated by network hardware and applications.
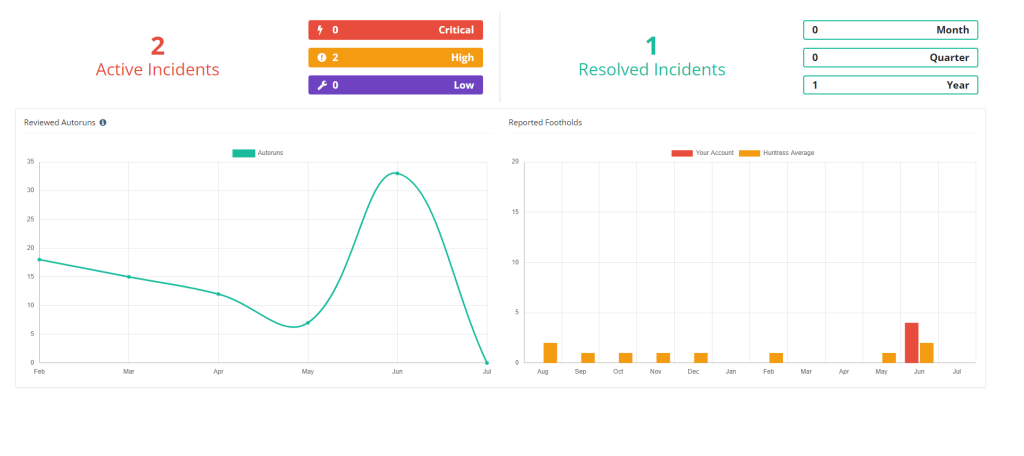
Our Numbers
Cost Effectiveness
We offer affordable IT solutions that help you reduce costs and improve your bottom line. Value Without Compromising Quality.
Innovative Technology
We always stay up-to-date with the latest technology trends and offer innovative solutions that help you stay ahead of the competition every time.
Industry expertise
We specialize in serving specific industries, such as construction, finance, manufacturing, and offer tailored solutions that meet your unique needs.

